WebListener web server implementation in ASP.NET Core
By Tom Dykstra and Chris Ross
[!NOTE] This topic applies only to ASP.NET Core 1.x. In ASP.NET Core 2.0, WebListener is named HTTP.sys.
WebListener is a web server for ASP.NET Core that runs only on Windows. It’s built on the Http.Sys kernel mode driver. WebListener is an alternative to Kestrel that can be used for direct connection to the Internet without relying on IIS as a reverse proxy server. In fact, WebListener can’t be used with IIS or IIS Express, as it isn’t compatible with the ASP.NET Core Module.
Although WebListener was developed for ASP.NET Core, it can be used directly in any .NET Core or .NET Framework application via the Microsoft.Net.Http.Server NuGet package.
WebListener supports the following features:
- (xref:)Windows Authentication
- Port sharing
- HTTPS with SNI
- HTTP/2 over TLS (Windows 10)
- Direct file transmission
- Response caching
- WebSockets (Windows 8)
Supported Windows versions:
- Windows 7 and Windows Server 2008 R2 and later
View or download sample code ((xref:)how to download)
When to use WebListener
WebListener is useful for deployments where you need to expose the server directly to the Internet without using IIS.
Because it’s built on Http.Sys, WebListener doesn’t require a reverse proxy server for protection against attacks. Http.Sys is mature technology that protects against many kinds of attacks and provides the robustness, security, and scalability of a full-featured web server. IIS itself runs as an HTTP listener on top of Http.Sys.
WebListener is also a good choice for internal deployments when you need one of the features it offers that you can’t get by using Kestrel.
How to use WebListener
Here’s an overview of setup tasks for the host OS and your ASP.NET Core application.
Configure Windows Server
Install the version of .NET that your application requires, such as .NET Core or .NET Framework 4.5.1.
Preregister URL prefixes to bind to WebListener, and set up SSL certificates
If you don’t preregister URL prefixes in Windows, you have to run your application with administrator privileges. The only exception is if you bind to localhost using HTTP (not HTTPS) with a port number greater than 1024; in that case administrator privileges aren’t required.
For details, see How to preregister prefixes and configure SSL later in this article.
Open firewall ports to allow traffic to reach WebListener.
You can use netsh.exe or PowerShell cmdlets.
There are also Http.Sys registry settings.
Configure your ASP.NET Core application
Install the NuGet package Microsoft.AspNetCore.Server.WebListener. This also installs Microsoft.Net.Http.Server as a dependency.
Call the
UseWebListenerextension method on WebHostBuilder in yourMainmethod, specifying any WebListener options and settings that you need, as shown in the following example:[!code-csharpMain]
1: using System;
2: using System.IO;
3: using Microsoft.AspNetCore.Hosting;
4: using Microsoft.Extensions.Configuration;
5: using Microsoft.Net.Http.Server;
6:7: // The default listening address is http://localhost:5000 if none is specified.
8: // Replace "localhost" with "*" to listen to external requests.
9: // You can use the --urls command-line flag to change the listening address. Ex:
10: // > dotnet run --urls http://*:8080;http://*:8081
11:12: // Use the following code to configure URLs in code:
13: // builder.UseUrls("http://*:8080", "http://*:8081");
14: // Put it after UseConfiguration(config) to take precedence over command-line configuration.
15:16: namespace WebListenerDemo
17: {18: /// <summary>
19: /// Executing the "dotnet run" command in the application folder will run this app.
20: /// </summary>
21: public class Program
22: {23: public static string Server;
24:25: #region snippet_Main
26: public static void Main(string[] args)
27: {28: Console.WriteLine("Running demo with WebListener.");
29:30: var config = new ConfigurationBuilder()
31: .AddCommandLine(args)32: .Build();33:34: var builder = new WebHostBuilder()
35: .UseContentRoot(Directory.GetCurrentDirectory())36: .UseConfiguration(config)37: .UseStartup<Startup>()38: .UseWebListener(options =>39: {40: options.ListenerSettings.Authentication.Schemes = AuthenticationSchemes.None;41: options.ListenerSettings.Authentication.AllowAnonymous = true;
42: });43:44: var host = builder.Build();45: host.Run();46: }47: #endregion
48: }49: }Configure URLs and ports to listen on
By default ASP.NET Core binds to
http://localhost:5000. To configure URL prefixes and ports, you can use theUseURLsextension method, theurlscommand-line argument or the ASP.NET Core configuration system. For more information, see Hosting.Web Listener uses the Http.Sys prefix string formats. There are no prefix string format requirements that are specific to WebListener.
[!NOTE] Make sure that you specify the same prefix strings in
UseUrlsthat you preregister on the server.Make sure your application is not configured to run IIS or IIS Express.
In Visual Studio, the default launch profile is for IIS Express. To run the project as a console application you have to manually change the selected profile, as shown in the following screen shot.
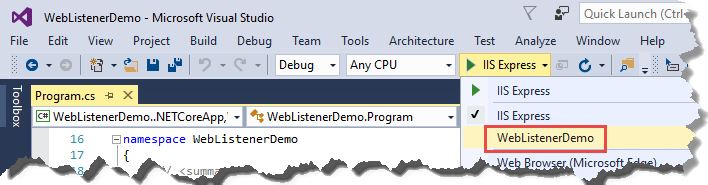
Select console app profile
How to use WebListener outside of ASP.NET Core
Install the Microsoft.Net.Http.Server NuGet package.
Preregister URL prefixes to bind to WebListener, and set up SSL certificates as you would for use in ASP.NET Core.
There are also Http.Sys registry settings.
Here’s a code sample that demonstrates WebListener use outside of ASP.NET Core:
var settings = new WebListenerSettings();
settings.UrlPrefixes.Add("http://localhost:8080");
using (WebListener listener = new WebListener(settings))
{
listener.Start();
while (true)
{
var context = await listener.AcceptAsync();
byte[] bytes = Encoding.ASCII.GetBytes("Hello World: " + DateTime.Now);
context.Response.ContentLength = bytes.Length;
context.Response.ContentType = "text/plain";
await context.Response.Body.WriteAsync(bytes, 0, bytes.Length);
context.Dispose();
}
}Preregister URL prefixes and configure SSL
Both IIS and WebListener rely on the underlying Http.Sys kernel mode driver to listen for requests and do initial processing. In IIS, the management UI gives you a relatively easy way to configure everything. However, if you’re using WebListener you need to configure Http.Sys yourself. The built-in tool for doing that is netsh.exe.
The most common tasks you need to use netsh.exe for are reserving URL prefixes and assigning SSL certificates.
NetSh.exe is not an easy tool to use for beginners. The following example shows the bare minimum needed to reserve URL prefixes for ports 80 and 443:
netsh http add urlacl url=http://+:80/ user=Users
netsh http add urlacl url=https://+:443/ user=UsersThe following example shows how to assign an SSL certificate:
netsh http add sslcert ipport=0.0.0.0:443 certhash=MyCertHash_Here appid={00000000-0000-0000-0000-000000000000}".Here is the official reference documentation:
The following resources provide detailed instructions for several scenarios. Articles that refer to HttpListener apply equally to WebListener, as both are based on Http.Sys.
- How to: Configure a Port with an SSL Certificate
- HTTPS Communication - HttpListener based Hosting and Client Certification This is a third-party blog and is fairly old but still has useful information.
- How To: Walkthrough Using HttpListener or Http Server unmanaged code (C++) as an SSL Simple Server This too is an older blog with useful information.
- How Do I Set Up A .NET Core WebListener With SSL?
Here are some third-party tools that can be easier to use than the netsh.exe command line. These are not provided by or endorsed by Microsoft. The tools run as administrator by default, since netsh.exe itself requires administrator privileges.
- http.sys Manager provides UI for listing and configuring SSL certificates and options, prefix reservations, and certificate trust lists.
- HttpConfig lets you list or configure SSL certificates and URL prefixes. The UI is more refined than http.sys Manager and exposes a few more configuration options, but otherwise it provides similar functionality. It cannot create a new certificate trust list (CTL), but can assign existing ones.
For generating self-signed SSL certificates, Microsoft provides command-line tools: MakeCert.exe and the PowerShell cmdlet New-SelfSignedCertificate. There are also third-party UI tools that make it easier for you to generate self-signed SSL certificates:
Next steps
For more information, see the following resources:
 )
)
|
|